I did some preliminary experimenting with password cracking utility John the Ripper to test the security of my own root password. I started by installing John and dumping the /etc/passwd file.
sudo apt-get install john
unshadow /etc/passwd /etc/shadow > mypasswd.txt
The mypasswd.txt file now holds a salted hash of my root password. I then passed this over to John to work its magic.
john mypasswd.txt
John is very powerful. I experimented with the most basic of cracking settings starting with single mode, then word lists and John would have moved to an incremental mode. I am happy to say I chose a sufficiently complex password that withstood John’s single crack mode and word lists.
Password cracking is very CPU intensive and the 10+ year old server that I am working with is probably about the least appropriate computer to attempt a rigorous cracking approach. The fan kicked on immediately and my laptop starting running hot. After more than 10 minutes of cracking attempts I aborted John and you can see the output below.
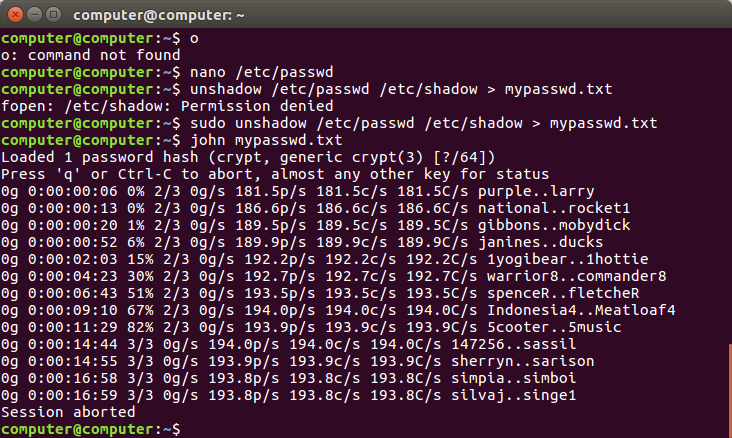
This was a fun and great learning exercise. I am going to continue experimenting with John. I will test John on the passwords stored in my Password Manager next. Using this technique I will also mount the Windows partition I have on my server and attempt to access and crack the Windows password hashes from Ubuntu.