The nmap stealth scan -sS flag allows you to search for open ports by adjusting the TCP/IP three way handshake:
The handshake ordinarily is SYN -> SYN ACK -> ACK
The -sS flags change the handshake to SYN -> SYN ACK -> RST
Defined: Synchronize, Acknowledge, Reset
This makes it less likely, but certainty not impossible for an intrusion detection system to pickup the scan.
The best approach that I can think of would be to use the -sS flag and between each port tested use Tor to change IPs from within a regionally anticipated region based on the purpose and location of the target. There is a great write up on how to do just that here using Tor and Proxy Chains to use public proxies.
The article also mentions using the tor-resolve feature to resolve a hostname to an IP address to avoid all of your queries going through the DNS server of the ISP. Nmap allows the -n flag to never use DNS name resolution and the -Pn flag to avoid host discovery.
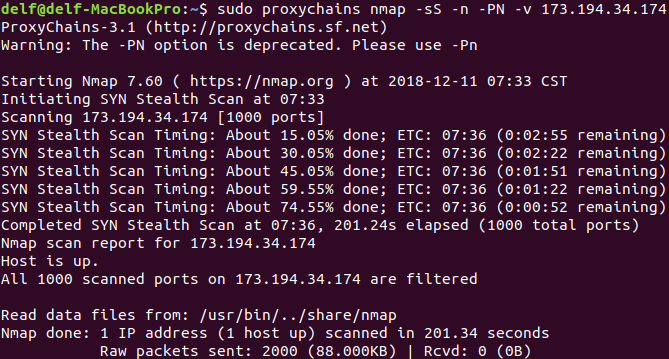
That leaves me with the following command after using tor-resolve on technicalagain.com: sudo proxychains nmap -sS -n -PN -v 173.194.34.174
Update: Also don’t forget the -O flag to learn the operating system and hosting service.