I’ve continued my experimentation with the Metasploitable (msf2) operating system as well as the Metasploit framework. I’m now up to five, I think, total successful exploits. I will write about two more of them here. The first, most basic, exploit I wrote about previously took advantage of a misconfigured rsh-server.
My next two exploits followed the same pattern:
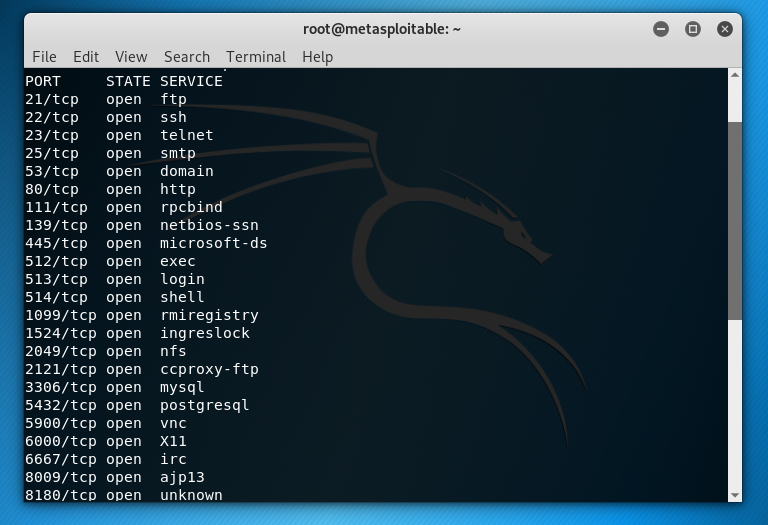
- Conduct an nmap scan to see what services are exposed.
- Find open ports and search Metasploit for a highly probable exploit or exploit + payload to open a reverse shell with root access
I was successful in exploiting the IRC server running on port 6667 and Java server running on port 5432.
I think the exploit of IRC server running on 6667 was added to msf2 just to give newbies like myself something to practice on. I see little point in running an IRC server in light of more modern collaborative technology and the exploit we used is very dated and specific:
unix/irc/unreal_ircd_3281_backdoor This module exploits a malicious backdoor that was added to the Unreal IRCD 3.2.8.1 download archive. This backdoor was present in the Unreal3.2.8.1.tar.gz archive between November 2009 and June 12th 2010.
This is a great first exploit for Metasploit because I got to learn the software and run it successfully. It was the simplest of configurations–set your remote host IP address and go. Nothing more.
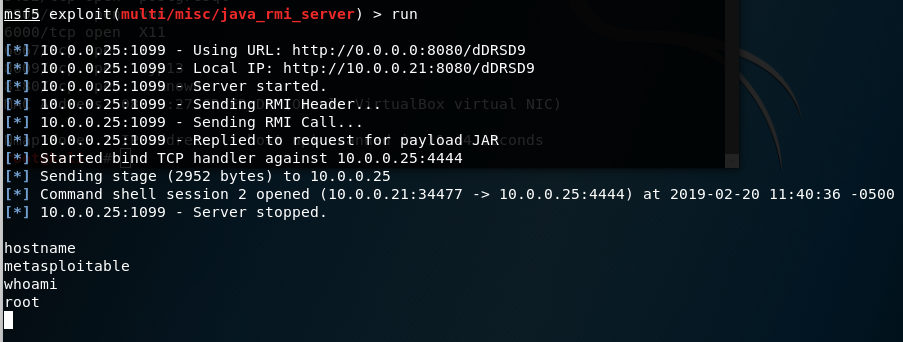
The second exploit I discovered is also dated (from 2011) and runs on Java. It was a little more complex.
multi/misc/java_rmi_server This module takes advantage of the default configuration of the RMI Registry and RMI Activation services, which allow loading classes from any remote (HTTP) URL. As it invokes a method in the RMI Distributed Garbage Collector which is available via every RMI endpoint, it can be used against both rmiregistry and rmid, and against most other (custom) RMI endpoints as well. Note that it does not work against Java Management Extension (JMX) ports since those do not support remote class loading, unless another RMI endpoint is active in the same Java process. RMI method calls do not support or require any sort of authentication.
This module requires picking and also delivering a payload. My first payload failed, a generic shell. The next payload I chose, a java reverse tcp shell, worked and I gained root access for the second time today.
Learnings
I’m getting more familiar with Metasploit as well as starting to see more clearly the holes in msf2. Up until this point I have resisted using Armitage, a visual UI for Metasploit, because I really wanted to learn about Metasploit directly. I think I will pick up Armitage soon if for nothing else, I think it will be a lot faster. I’m resisting the urge to just let Metasploit do all the thinking for me. I am intentional on what exploits I use and then trying to really understand why they do or do not work.
Update: I’ve since gained access to Postgres through the server and used psql to create/alter users and browse the tables. I want to be thoughtful to make sure I keep learning. I will not just get locked into the pattern of nmap >> metasploit >> root shell. I was disappointed to see there wasn’t any fun data inside the postgres tables in msf2 and so no real incentive to learn how to exfiltrate the data.
I suspect many Metasploit users hit the stage I’m at pretty early on. Which is a lot of enthusiasm for hitting pay dirt occasionally, and the draw to stay locked in the same exploit pattern.